Enabling and Using Synced Passkeys in Entra ID
- Gabriel Delaney
- Nov 22, 2025
- 3 min read
Updated: Dec 19, 2025

I love synced passkeys.
I use them anywhere that accepts them, because they are more seamless than passwords and far more resistant to phishing. They are not as strong as device bound keys, but they are still a meaningful improvement for both security and usability. When Microsoft enabled synced passkeys in public preview I immediately opted into the preview.
That said, synced passkeys have real limitations. Entra cannot enforce attestation for them, the security of the passkey is directly tied to the security of the password manager that stores it. That does not mean they are unsafe. It just means you should introduce them deliberately, in controlled scenarios, and with clear boundaries.
In this article I show you how to enable synced passkeys using Keeper Password Manager as an example. I have also set it up with Google Password Manager, and the setup is similar across password managers, although each solution has its own minor idiosyncrasies.
Enabling Synced Passkeys in Entra
Before we get started make sure you opt in to the Passkey profile (preview).
1. Open the Authentication Methods policies Go to Security, then Authentication Methods, then Policies.
2. Open the Passkey (FIDO2) method Select Passkey (FIDO2) and switch to Configure.
3. Create a dedicated passkey profile Create a new profile called Allow Synced Passkeys. This profile will allow both device bound and synced passkeys. In the Default profile, turn off synced passkeys so you can fully control usage.
4. Restrict which synced passkeys are allowed In the Allow Synced Passkeys profile, limit the accepted AAGUIDs to the providers you plan to test.
For this demo I allowed:
Microsoft Authenticator
Google Password Manager: ea9b8d66-4d01-1d21-3ce4-b6b48cb575d4
Keeper: 0ea242b4-43c4-4a1b-8b17-dd6d0b6baec6
Why Google and Keeper? Honestly, because that is what I had available. I have a Google Workspace tenant and I already use Keeper. That is it. The point is not which vendors you pick. It is that you limit the AAGUIDs so you know exactly what synced passkeys you are introducing into your environment.

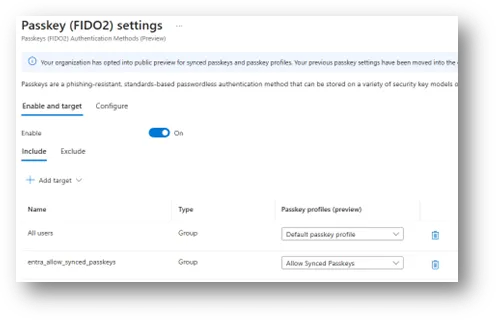
5. Assign the profile to a group Go to Passkey (FIDO2) > Enable and target. Enable the method, choose Include, and target a group. Assign the Allow Synced Passkeys profile to that group.
Registering a Synced Passkey with Keeper
If you’ve registered a passkey before, most of these instructions will be pretty familiar to you.
1. Open Security info Go to https://mysignins.microsoft.com/security-info and select Add sign-in method. Choose Passkey.

2. Begin the passkey setup You will see the standard Microsoft passkey setup prompt. Select Next.

3. Keeper prompts to create a passkey WebAuthn triggers, the Keeper extension intercepts the request, and you get the Create Login with Passkey dialog. Select Create Passkey.

4. Name the passkey Entra asks you to name the key so you can identify it later. Enter a name such as Keeper and select Next.

5. Passkey creation completes You receive the confirmation screen. Select Done.

6. Now, let’s test the passkey by signing in Go to https://login.microsoftonline.com, enter your email, and choose Face, fingerprint, PIN or security key Passkey.

Keeper will surface the newly created passkey. Select Use Passkey it to authenticate.

A successful sign in confirms the Keeper synced passkey is working as expected.
Security Considerations
Synced passkeys are better than passwords, but in my opinion they are not as secure as device bound passkeys or hardware backed FIDO2 keys.
Appropriate Use Cases
Standard users
BYOD environments
If you have an Enterprise password manager.
Where Synced Passkeys Should Not Be Used
Privileged roles
Break glass accounts
Recommendations for a Controlled Deployment
Enablement for a group
Restricted profile with selected AAGUIDs
Final Thoughts
Synced passkeys are a significant improvement over passwords. They are not a replacement for device bound or hardware backed credentials, but they can serve an important role in a broader passwordless strategy.



Any extended thoughts on why Synced Passkeys should not be used for Privileged roles or Break glass accounts?
I would think device-bound should be preferred, but if the org is currently using a mix of Passkey and non-phishing resistant, Passkeys, even for privileged roles, are a huge security upgrade.